Sri Lanka CERT has issued a further update on the warning they issued for malicious One Time Password (OTP) SMS’s originating from local private numbers instead of respective authentication service providers.
Sri Lanka CERT statement
Further Update: OTP’s sent via a Local Private Number
Threat Level
Medium
Overview
Further to our previous alert on the same subject matter there has been some misunderstanding relating to the impact due to this type of incidents, that have been reported to CERT. This update is to ensure that there is no misinterpretation or confusion with respect to the previous alert.
Sri Lanka CERT|CC has received numerous complaints from the general public expressing concern about receiving OTP messages from local (unknown) private numbers instead of from their usual trusted authentication service providers. Further it was reported that some of these SMS service providers have maliciously obtained user account details pretending to be their usual authentication service provider. As a result, some of these social media accounts have been compromised.
Description
One Time Password (OTP) is a service that provides an extra layer of security. This is mostly used when accessing accounts and carrying out financial transactions etc. to identify the real user of the account. When a service provider sends an OTP to a customer, it comes as an SMS message and the displayed sender name of that OTP message will be the actual service provider. E.g. If you request an OTP from Google, sender of that OTP would be Google itself and you will receive a message from Google.
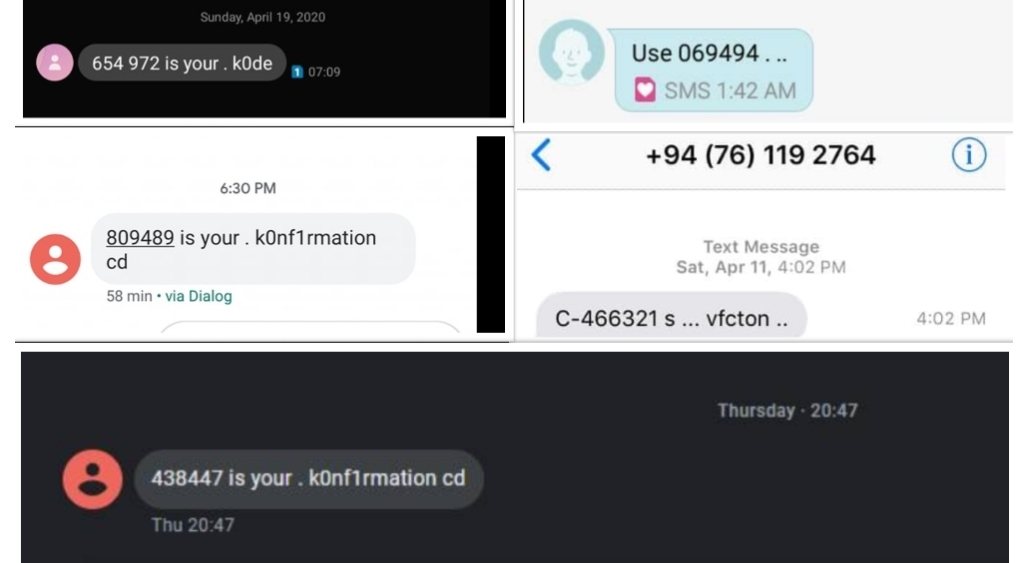
If you receive your OTP from a local private number, instead of from your usual service provider’s name it means that the message has come through a third-party SMS provider. They normally change its content slightly except the OTP code and send it to the user through a private number. Please refer below images for examples, where there are deliberate spelling mistakes made and the word “OTP” is not used – in order to bypass detection by legitimate service providers.
There have been several reports about malicious third party SMS Gateway service providers who have attempted to obtain account details (user names, password etc.) by having further communication with customers pretending to be the legitimate service provider by building trust using the OTP message. Sri Lanka CERT has received numerous complaints of such compromised accounts, after investigation it was discovered that account details have been provided to malicious third party SMS service providers after receiving the OTP.
Impact
- Potential risk of your online accounts such as social media, emails, online banking, etc. being compromised, in the event that you mistakenly disclose your account credentials or personal details to third party SMS service providers who pretend to be your trusted service provider.
Solution/ Workarounds
- Do not disclose any of your account credentials or personal details to the third-party SMS providers or anyone else by any means (Calls, SMS, Emails, etc.)
- Frequently change your passwords and setup proper account recovery options.
Disclaimer
The information provided herein is on “as is” basis, without warranty of any kind.